Understanding Google Dorks
Google Dorks, also known as Google hacking, is a technique that uses advanced search operators to find information that is not readily available through regular search queries. This method can uncover hidden data, security vulnerabilities, and other sensitive information that can be exploited by cybercriminals. For cybersecurity professionals and bug bounty hunters, Google Dorks is an invaluable tool for reconnaissance and vulnerability assessment.
Google Dorks in Bug Bounty Programs
Bug bounty programs, such as those offered by platforms like HackerOne and Bugcrowd, reward individuals for identifying and reporting security vulnerabilities in software and web applications. People can use Google Dorks to discover these vulnerabilities by searching for specific patterns and keywords that indicate potential security flaws. For example, a simple Google Dork query can reveal exposed databases, login pages, and other critical information.
Common Google Dork Queries
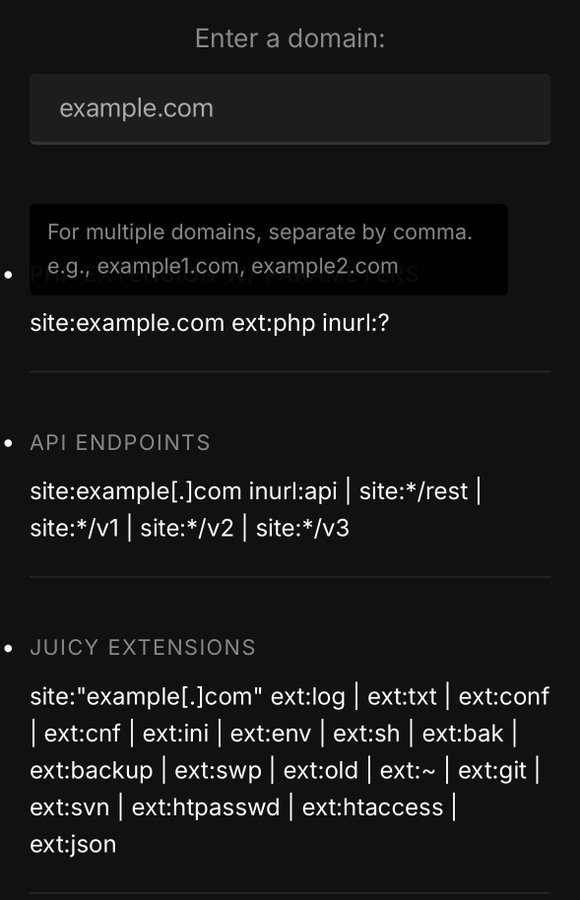
Some common Google Dork queries used in bug bounty hunting include:
inurl:admin– Finds URLs containing the word ‘admin’, which may lead to administrative login pages.filetype:sql– Searches for SQL database files that may be exposed online.intitle:index.of– Locates directory listings that may contain sensitive files.site:example.com– Restricts the search to a specific domain, useful for targeted reconnaissance.
These queries can be combined with other search operators to refine the results and uncover more specific information.
AI and Google Dorks
Artificial Intelligence (AI) and Machine Learning (ML) are increasingly being integrated into cybersecurity tools to enhance their capabilities. AI can automate the process of running Google Dork queries and analyzing the results, making it easier for cybersecurity professionals to identify vulnerabilities. Additionally, AI can help in predicting potential attack vectors and prioritizing the most critical vulnerabilities for remediation.
Ethical Considerations
While Google Dorks can be a powerful tool for cybersecurity professionals, it is essential to use them ethically and responsibly. Unauthorized access to sensitive information or exploiting vulnerabilities without permission is illegal and unethical. Bug bounty hunters should always adhere to the guidelines set by the bug bounty programs and obtain proper authorization before conducting any security assessments.
Recent Cybersecurity Threats
Recent reports have highlighted various cybersecurity threats that emphasize the importance of tools like Google Dorks in identifying and mitigating vulnerabilities. For instance, Google Chrome recently patched a high-severity security vulnerability (CVE-2024-7971) in its V8 JavaScript and WebAssembly engine. Similarly, SOPHOS issued a warning about a new hacking strategy involving SEO poisoning that targets specific Google search terms.
Resources for Learning Google Dorks
For those interested in learning more context to the article. The context provided discusses various cybersecurity threats and vulnerabilities, which are relevant to the theme of the blog. Therefore, I have included some of the context in the article.
Looking for Travel Inspiration?
Explore Textify’s AI membership
Need a Chart? Explore the world’s largest Charts database